
To ensure the company’s information security and the high availability of its systems, the company has been continuously investing in information security over the past few years. It has established an Information Security Management Team and, in accordance with the National Cyber Security Level Assessment (S3A3) requirements, has developed an Information Security Management System and Information Security Management Practical Rules. The Information Department and the Audit Department regularly inspect and audit the implementation of various information security-related measures to minimize the risk of information security incidents.
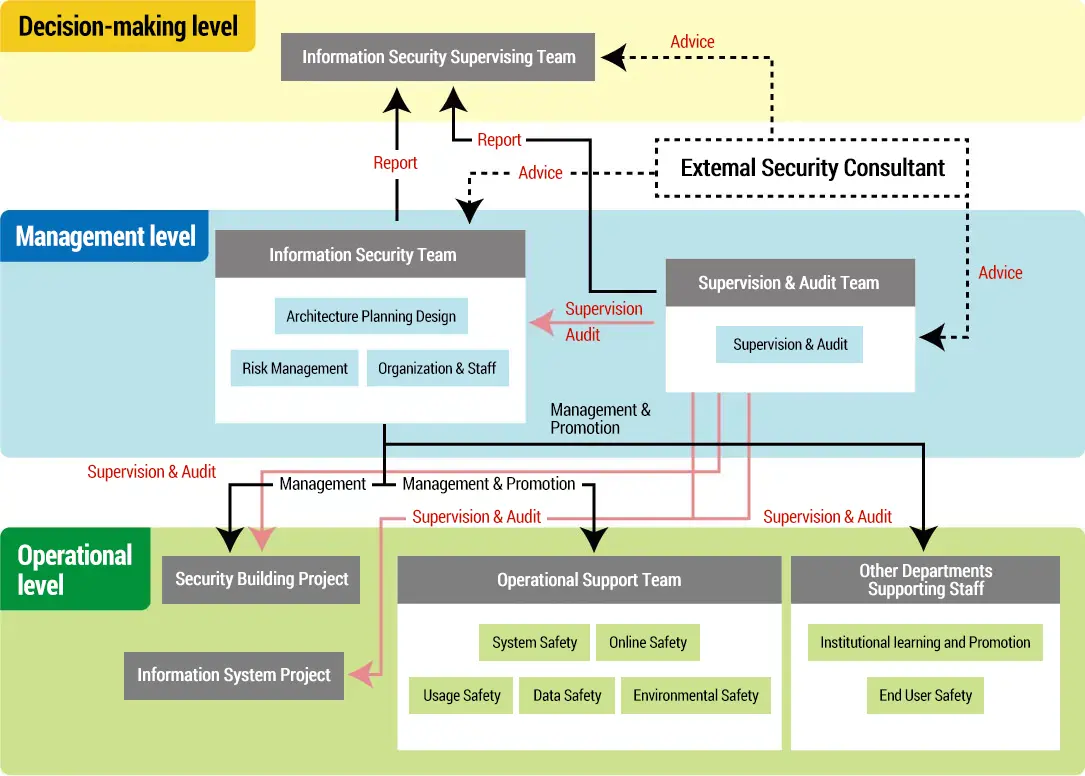
In response to the dynamic nature of our business operations and diversified transaction models, we strictly adhere to Taiwan’s Personal Data Protection Act, and to China’s Data Security Law and Information Security Classified Protection 2.0 Standards. To enhance information security, prevent data breaches, and mitigate transaction risks, we have reinforced protections across our proprietary systems—“Chlitina Store Management System” and “Chlitina Portal System”—through the following measures:
-Optimization of Access Control: Restricted permissions for sensitive data access;
-Introduction of an Audit Log System: Real-time monitoring and recording of operational activities;
-Implementation of a Security Platform: Advanced defense mechanisms to minimize cybersecurity risks.
These upgrades significantly reduce risks of customer data exposure and transaction vulnerabilities while ensuring stable, secure, and compliant digital operations.
To secure the Company’s data assets and ensure business continuity, the Company has upgraded hardware and software related to cyber security, data backup, and network access in the last three years. We have conducted measurement and quantitative analysis of information security indicators based on audit results and performed information security assessment through regular information security simulation drills to ensure the continuous effectiveness of information security measures.
| Number of security incidents and fines per year | 2021 | 2022 | 2023 | 2024 |
|
Number of security or network security incidents |
0 | 0 | 0 | 0 |
| Number of data breach incidents | 0 | 0 | 0 | 0 |
| Number of security incidents involving customer personal data | 0 | 0 | 0 | 0 |
| Number of customers and employees affected by incidents or data breaches | 0 | 0 | 0 | 0 |
| Amount of fines for information security or network security related incidents | 0 | 0 | 0 | 0 |
| Number of security or network security incidents | 2021 | 2022 | 2023 | 2024 |
|
Number of data breach incidents |
0 | 0 | 0 | 0 |
| Number of data breach incidents | 0 | 0 | 0 | 0 |
| Number of security incidents involving customer personal data | 0 | 0 | 0 | 0 |
| Number of customers and employees affected by incidents or data breaches | 0 | 0 | 0 | 0 |
| Amount of fines for information security or network security related incidents | 0 | 0 | 0 | 0 |